TLS-SSL-Protocols: Difference between revisions
(Initial page) |
|||
| (26 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
As a way to mitigate the [https://www.openssl.org/~bodo/ssl-poodle.pdf Padding Oracle | As a way to mitigate the [https://www.openssl.org/~bodo/ssl-poodle.pdf Padding Oracle On Downgraded Legacy Encryption (POODLE) attack], information technology (IT) administrators can disable all protocols older than TLSv1 via ActiveDirectory group policies. This page describes how to do that. | ||
Using the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible | Using the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible policy template] with the group policy editor allows IT administrators to deploy computer-level policies that disable legacy protocols within Windows Schannel and deploy user-level policies that disable legacy protocols within Internet Explorer. Note that a computer-level disable policy for a protocol overrides Internet Explorer's configuration for that protocol. | ||
This template implements [https://technet.microsoft.com/en-us/library/security/3009008.aspx#sectionToggle3 Microsoft's recommended registry settings to disable SSLv3]. | |||
== | Please note that Microsoft has a group policy setting for disabling TLS/SSL protocols in Internet Explorer, as described in the "Disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 for Internet Explorer in Group Policy" section of [https://technet.microsoft.com/en-us/library/security/3009008.aspx#sectionToggle3 their recommendations], but it doesn't work reliably with Internet Explorer 6 or 7. As a result, Microsoft noted in their policy template that it works only with Internet Explorer 8 and higher. If you run Internet Explorer 6 or 7, then the group policy template described on this page is a tenable option for you. The computer policies in this policy template are also useful to IT administrators whom are targeting only Internet Explorer 8 or higher. | ||
To handle systems that are not covered by group policies, this page also includes registry merge files for convenience. | |||
==Configure With Group Policies== | |||
To use the group policies, you'll need to install the policy template file. The policy template includes two group policy targets for configuration: Computer and User. | |||
===Installation=== | |||
Save the [https://www.moonlightdesign.org/dl/TLS-SSL-Protocols.adm Windows Server 2003 compatible policy template] as TLS-SSL-Protocols.adm within your Windows INF folder. This is typically <code>C:\Windows\INF</code>. | |||
===Computer Policies=== | ===Computer Policies=== | ||
| Line 13: | Line 19: | ||
Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies. | Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies. | ||
To get started, either create a new group policy or edit an existing group policy that applies to groups of computers. The computer policy won't have an effect if it applies only to users and not to computers. | |||
====Add the Policy Template==== | |||
Right-click on the Computer Configuration | Administrative Templates folder. Alternatively, right-clicking on the User Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item. | |||
[[File:AddTemplate1.png|650px]] | |||
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed. | |||
[[File:AddTemplate2.png|370px]] | |||
Select the TLS-SSL-Protocols.adm file and click the Open button. | |||
[[File:AddTemplate3.png|475px]] | |||
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue. | |||
[[File:AddTemplate4.png|370px]] | |||
====Show All Policy Settings==== | |||
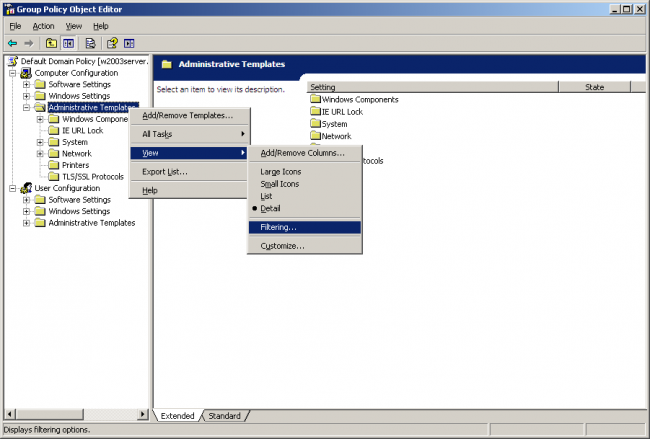
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the Computer Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item. | |||
[[File:Filtering-Computer.png|650px]] | |||
In the Filtering dialog, uncheck the "Only show policy settings that can be fully managed" checkbox. Click OK. | |||
[[File:Filtering.png|350px]] | |||
====TLS/SSL Protocols==== | |||
Open the TLS/SSL Protocols folder within the Computer Configuration | Administrative Templates folder. A list of policy settings should appear. If it is empty, then the view filtering might be hiding them. Please follow the instructions above if that is happening. | |||
[[File:Policies-Computer.png|650px]] | |||
If you have Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier systems, then enable TLS 1.0 for client and server use while disabling PCT 1.0, SSL 2.0, and SSL 3.0 for client and server use. The screenshot above shows what this configuration looks like. | |||
The Group Policy Editor makes configuration convenient with the Next Setting button, as shown in the screenshot below. Starting with the first setting, position the dialog box such that the recommendation for that setting at the top of the "Description:" line is visible. Apply that recommendation to every setting in this list, clicking Next Setting to navigate to the next setting. Click OK when done. After clicking OK, this group policy is ready to get picked up by computers upon their next application of the computer group policies to their local computer. Running gpupdate.exe on the computers that have this group policy assigned to them will cause them to pick up the change before gpupdate.exe returns. | |||
[[File:Policies-Computer-SSLv3Client.png|650px]] | |||
If your network is comprised entirely of Windows Server 2008 R2, Windows 7, or newer operating systems, then disabling TLS 1.0 can theoretically improve security further, but when this was tested in Windows 8 with Internet Explorer 11, Internet Explorer 11 wouldn't start up successfully until TLS 1.0 was enabled in Schannel. As a result, TLS 1.0 will need to be left enabled in Windows Schannel, even if it's disabled in Internet Explorer. | |||
===User Policy=== | |||
The User policy configures Internet Explorer and has been tested with versions 6 and higher. If you are targeting only Internet Explorer 8 or higher, it is recommended that you instead use the group policy for disabling TLS/SSL protocols as documented in the "Disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 for Internet Explorer in Group Policy" section of [https://technet.microsoft.com/en-us/library/security/3009008.aspx#sectionToggle3 Microsoft's recommendations for mitigating the POODLE attack]. Microsoft's built-in group policy, however, doesn't work reliably with Internet Explorer 6 and 7. | |||
To get started, either create a new group policy or edit an existing group policy that applies to groups of users. The user policy won't have an effect if it applies only to computers and not to users. | |||
====Add the Policy Template==== | |||
Right-click on the User Configuration | Administrative Templates folder. Alternatively, right-clicking on the Computer Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item. | |||
[[File:AddTemplate1.png|650px]] | |||
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed. | |||
[[File:AddTemplate2.png|370px]] | |||
Select the TLS-SSL-Protocols.adm file and click the Open button. | |||
[[File:AddTemplate3.png|475px]] | |||
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue. | |||
[[File:AddTemplate4.png|370px]] | |||
====Show All Policy Settings==== | |||
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the User Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item. | |||
[[File:Filtering-User.png|650px]] | |||
In the Filtering dialog, uncheck the "Only show policy settings that can be fully managed" checkbox. Click OK. | |||
[[File:Filtering.png|350px]] | |||
====TLS/SSL Protocols==== | |||
Open the TLS/SSL Protocols folder within the User Configuration | Administrative Templates folder. A list of policy settings should appear. If it is empty, then the view filtering might be hiding them. Please follow the instructions above if that is happening. | |||
[[File:Policies-User.png|650px]] | |||
Edit the policy setting and choose the Enabled radio button. | |||
If you have Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier systems, then choose the Recommended item. Although those operating systems don't implement TLS 1.1 and 1.2, enabling TLS 1.1 and 1.2 is properly ignored by those older operating systems while being enabled on Windows 7, Windows Server 2008 R2, and newer operating systems. | |||
If all systems on your network run Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier, then the Windows Vista/XP option is feasible as that enables only TLS 1.0, but it's typically best to choose Recommended as that will allow upgraded systems to prefer TLS 1.1 and 1.2. | |||
If all systems on your network run Windows 7, Windows Server 2008 R2, or newer operating systems, then the Recommended setting works, but the Windows 7 Best Security and Windows 7 Good Security items provide stronger security. If you choose Windows 7 Best Security, then only TLS 1.2 will be used, and that will give your secure connections maximum protection against known attacks. If some web sites that your organization use support TLS 1.1 as their highest protocol, then the Windows 7 Good Security item enables TLS 1.1 while preferring TLS 1.2. Some web sites may support only TLS 1.0 as their strongest option, and working with such web sites requires choosing the Recommended item. | |||
The Insecure and Highly Insecure items should never be used for medium or long term production use. They are present primarily for testing and as a short-term fallback if needed. Don't use them unless if it's absolutely necessary for a short time period. While enabled, your secure connections will effectively be as secure as using no encryption at all, even if Internet Explorer is using TLS 1.0 or higher. It's possible for a downgrade attack to cause Internet Explorer or the remote server to drop down to SSL 3.0, and disabling SSL 3.0 entirely is an effective mitigation against a downgrade attack to SSL 3.0. | |||
[[File:Policies-User-IE.png|375px]] | |||
Click OK when done. After clicking OK, this group policy is ready to get picked up by users upon their next application of the user group policies. Having the users log out and back in or having the users run gpupdate.exe will cause them to pick up the change. | |||
Please note that users can update this setting within Internet Explorer's configuration options. This policy won't overwrite their customizations unless if this policy is changed to another value or if all policies are reapplied to that user, such as with 'gpupdate /force'. | |||
==Configure Without Group Policies== | |||
To quickly configure a computer that doesn't have group policies, it is possible to use a registry merge file. The following files implement their stated configuration scenarios: | |||
*[https://www.moonlightdesign.org/dl/TLS1-1.2.reg Recommended: TLS 1.2, 1.1, and 1.0] | |||
**Compatible with all versions of Windows that implement TLS 1.0, including those that don't implement TLS 1.1 and 1.2. | |||
*[https://www.moonlightdesign.org/dl/TLS1.2.reg Windows 7 Best Security: TLS 1.2 only] | |||
**A shrinking number of web sites on the Internet won't work with this configuration. | |||
*[https://www.moonlightdesign.org/dl/TLS1-1.2.reg Windows 7 Good Security: TLS 1.2 and 1.1] | |||
**A shrinking number of web sites on the Internet won't work with this configuration. | |||
*[https://www.moonlightdesign.org/dl/TLS-SSL-Windows-Vista-XP.reg Windows Vista/XP: TLS 1.0 Only] | |||
**Don't use this on Windows 7, Windows Server 2008 R2, or newer as it disables TLS 1.1 and TLS 1.2 in Internet Explorer. | |||
*[https://www.moonlightdesign.org/dl/TLS-SSL-Insecure.reg Insecure: SSL 3.0 and TLS 1.0] | |||
**Don't use this unless if absolutely necessary. This configuration opens up your https connections to attack and should be considered equivalent to having no encryption. | |||
*[https://www.moonlightdesign.org/dl/TLS-SSL-Highly-Insecure.reg Highly Insecure: SSL 3.0 only] | |||
**Don't use this unless if absolutely necessary. This configuration opens up your https connections to attack and should be considered equivalent to having no encryption. | |||
**TLS 1.0 remains enabled in Windows Schannel, but it's off in Internet Explorer with this file. | |||
Latest revision as of 01:37, 7 December 2015
As a way to mitigate the Padding Oracle On Downgraded Legacy Encryption (POODLE) attack, information technology (IT) administrators can disable all protocols older than TLSv1 via ActiveDirectory group policies. This page describes how to do that.
Using the Windows Server 2003 compatible policy template with the group policy editor allows IT administrators to deploy computer-level policies that disable legacy protocols within Windows Schannel and deploy user-level policies that disable legacy protocols within Internet Explorer. Note that a computer-level disable policy for a protocol overrides Internet Explorer's configuration for that protocol.
This template implements Microsoft's recommended registry settings to disable SSLv3.
Please note that Microsoft has a group policy setting for disabling TLS/SSL protocols in Internet Explorer, as described in the "Disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 for Internet Explorer in Group Policy" section of their recommendations, but it doesn't work reliably with Internet Explorer 6 or 7. As a result, Microsoft noted in their policy template that it works only with Internet Explorer 8 and higher. If you run Internet Explorer 6 or 7, then the group policy template described on this page is a tenable option for you. The computer policies in this policy template are also useful to IT administrators whom are targeting only Internet Explorer 8 or higher.
To handle systems that are not covered by group policies, this page also includes registry merge files for convenience.
Configure With Group Policies
To use the group policies, you'll need to install the policy template file. The policy template includes two group policy targets for configuration: Computer and User.
Installation
Save the Windows Server 2003 compatible policy template as TLS-SSL-Protocols.adm within your Windows INF folder. This is typically C:\Windows\INF.
Computer Policies
The Computer policies configure the Windows Schannel protocol support, which impacts client software and server software with dedicated settings for each. Internet Explorer, email software, and any program that connects to the local network or Internet and uses Windows Schannel for securing its connections are affected by the client policies. Internet Information Server, .NET server software, and any program that listens for and accepts secure connections from the local network or Internet and uses Windows Schannel for securing connections are affected by the server policies.
Mozilla Firefox, Google Chrome, and Java, however, use their own software for securing connections and aren't affected by the client policies. Similarly, Java and software that uses OpenSSL (Apache, etc) or other non-Schannel software aren't affected by the server policies.
To get started, either create a new group policy or edit an existing group policy that applies to groups of computers. The computer policy won't have an effect if it applies only to users and not to computers.
Add the Policy Template
Right-click on the Computer Configuration | Administrative Templates folder. Alternatively, right-clicking on the User Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item.
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed.
Select the TLS-SSL-Protocols.adm file and click the Open button.
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue.
Show All Policy Settings
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the Computer Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item.
In the Filtering dialog, uncheck the "Only show policy settings that can be fully managed" checkbox. Click OK.
TLS/SSL Protocols
Open the TLS/SSL Protocols folder within the Computer Configuration | Administrative Templates folder. A list of policy settings should appear. If it is empty, then the view filtering might be hiding them. Please follow the instructions above if that is happening.
If you have Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier systems, then enable TLS 1.0 for client and server use while disabling PCT 1.0, SSL 2.0, and SSL 3.0 for client and server use. The screenshot above shows what this configuration looks like.
The Group Policy Editor makes configuration convenient with the Next Setting button, as shown in the screenshot below. Starting with the first setting, position the dialog box such that the recommendation for that setting at the top of the "Description:" line is visible. Apply that recommendation to every setting in this list, clicking Next Setting to navigate to the next setting. Click OK when done. After clicking OK, this group policy is ready to get picked up by computers upon their next application of the computer group policies to their local computer. Running gpupdate.exe on the computers that have this group policy assigned to them will cause them to pick up the change before gpupdate.exe returns.
If your network is comprised entirely of Windows Server 2008 R2, Windows 7, or newer operating systems, then disabling TLS 1.0 can theoretically improve security further, but when this was tested in Windows 8 with Internet Explorer 11, Internet Explorer 11 wouldn't start up successfully until TLS 1.0 was enabled in Schannel. As a result, TLS 1.0 will need to be left enabled in Windows Schannel, even if it's disabled in Internet Explorer.
User Policy
The User policy configures Internet Explorer and has been tested with versions 6 and higher. If you are targeting only Internet Explorer 8 or higher, it is recommended that you instead use the group policy for disabling TLS/SSL protocols as documented in the "Disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 for Internet Explorer in Group Policy" section of Microsoft's recommendations for mitigating the POODLE attack. Microsoft's built-in group policy, however, doesn't work reliably with Internet Explorer 6 and 7.
To get started, either create a new group policy or edit an existing group policy that applies to groups of users. The user policy won't have an effect if it applies only to computers and not to users.
Add the Policy Template
Right-click on the User Configuration | Administrative Templates folder. Alternatively, right-clicking on the Computer Configuration | Administrative Templates folder also works as it yields the same end-result. Click on the "Add/Remove Templates..." menu item.
In the Add/Remove Templates dialog, click on the "Add..." button if the TLS-SSL-Protocols policy template isn't listed.
Select the TLS-SSL-Protocols.adm file and click the Open button.
The Add/Remove Templates dialog should now list the TLS-SSL-Protocols policy template. Press the Close button to continue.
Show All Policy Settings
By default, the Group Policy Editor doesn't display policy settings that live outside of the group policy registry trees. The settings in this policy template live outside of the group policy registry trees, so you will need to change the view filtering. To do this, right-click on the User Configuration | Administrative Templates folder, click on the View submenu, and click on the "Filtering..." menu item.
In the Filtering dialog, uncheck the "Only show policy settings that can be fully managed" checkbox. Click OK.
TLS/SSL Protocols
Open the TLS/SSL Protocols folder within the User Configuration | Administrative Templates folder. A list of policy settings should appear. If it is empty, then the view filtering might be hiding them. Please follow the instructions above if that is happening.
Edit the policy setting and choose the Enabled radio button.
If you have Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier systems, then choose the Recommended item. Although those operating systems don't implement TLS 1.1 and 1.2, enabling TLS 1.1 and 1.2 is properly ignored by those older operating systems while being enabled on Windows 7, Windows Server 2008 R2, and newer operating systems.
If all systems on your network run Windows XP, Vista, 2008 (without R2), 2003, 2000, NT4, or earlier, then the Windows Vista/XP option is feasible as that enables only TLS 1.0, but it's typically best to choose Recommended as that will allow upgraded systems to prefer TLS 1.1 and 1.2.
If all systems on your network run Windows 7, Windows Server 2008 R2, or newer operating systems, then the Recommended setting works, but the Windows 7 Best Security and Windows 7 Good Security items provide stronger security. If you choose Windows 7 Best Security, then only TLS 1.2 will be used, and that will give your secure connections maximum protection against known attacks. If some web sites that your organization use support TLS 1.1 as their highest protocol, then the Windows 7 Good Security item enables TLS 1.1 while preferring TLS 1.2. Some web sites may support only TLS 1.0 as their strongest option, and working with such web sites requires choosing the Recommended item.
The Insecure and Highly Insecure items should never be used for medium or long term production use. They are present primarily for testing and as a short-term fallback if needed. Don't use them unless if it's absolutely necessary for a short time period. While enabled, your secure connections will effectively be as secure as using no encryption at all, even if Internet Explorer is using TLS 1.0 or higher. It's possible for a downgrade attack to cause Internet Explorer or the remote server to drop down to SSL 3.0, and disabling SSL 3.0 entirely is an effective mitigation against a downgrade attack to SSL 3.0.
Click OK when done. After clicking OK, this group policy is ready to get picked up by users upon their next application of the user group policies. Having the users log out and back in or having the users run gpupdate.exe will cause them to pick up the change.
Please note that users can update this setting within Internet Explorer's configuration options. This policy won't overwrite their customizations unless if this policy is changed to another value or if all policies are reapplied to that user, such as with 'gpupdate /force'.
Configure Without Group Policies
To quickly configure a computer that doesn't have group policies, it is possible to use a registry merge file. The following files implement their stated configuration scenarios:
- Recommended: TLS 1.2, 1.1, and 1.0
- Compatible with all versions of Windows that implement TLS 1.0, including those that don't implement TLS 1.1 and 1.2.
- Windows 7 Best Security: TLS 1.2 only
- A shrinking number of web sites on the Internet won't work with this configuration.
- Windows 7 Good Security: TLS 1.2 and 1.1
- A shrinking number of web sites on the Internet won't work with this configuration.
- Windows Vista/XP: TLS 1.0 Only
- Don't use this on Windows 7, Windows Server 2008 R2, or newer as it disables TLS 1.1 and TLS 1.2 in Internet Explorer.
- Insecure: SSL 3.0 and TLS 1.0
- Don't use this unless if absolutely necessary. This configuration opens up your https connections to attack and should be considered equivalent to having no encryption.
- Highly Insecure: SSL 3.0 only
- Don't use this unless if absolutely necessary. This configuration opens up your https connections to attack and should be considered equivalent to having no encryption.
- TLS 1.0 remains enabled in Windows Schannel, but it's off in Internet Explorer with this file.